After a long time in proof of concept and development, we’re happy to share our first product release, exclusive for beta testers, release 0.2024.1.
What’s New?
Laying the foundations of future releases, we’ve been building out our platform’s infrastructure and product with the beginnings of our web app, APIs and honeypot management systems.
Authentication API
Forming the basis of authentication and authorization for our product, we’ve build a dynamic authentication mechanism.
We had a number of key requirements in mind for our authentication to allow us to build out our product with features applicable to our target customers, business and enterprises, while also allowing individuals to have access.
To this end, our authentication system supports the grouping of individual users under accounts/organizations. In the future, this will allow customers to invite their team members to their organization’s account for access control. We’ve also build a way for individuals to have their own personal accounts, allowing anyone to consume our threat intelligence.
We’ve paired out authentication API with an industry leading IdP (Identity Provider) Auth0, offloading the actual user management side of the process and ensuring future integrations with Social and SSO (Single Sign On) providers is quick, seamless and easy.
{
"data": [
{
"accounts": [
"3f475ea2-2fa0-4345-8095-dcf6544fb77a"
],
"added": "2024-06-28T10:54:04.550654",
"admin_for": [
"3f475ea2-2fa0-4345-8095-dcf6544fb77a"
],
"id": "8f8d7d0e-a5f9-40a6-9894-50247e4ae008",
"metadata": {
"email": "32bitbradley@gmail.com",
"first_name": "Brad",
"last_name": "King",
"picture": "https://s.gravatar.com/avatar/1a697f0fa4a53f7595194c9c147978c0?s=480"
},
"modified": "2024-06-28T10:54:04.550654",
"reference": "auth0|6511862dd10104e2fa6f6412"
}
],
"error": 0,
"message": "User returned",
"meta": {
"items": 1,
"selection": {
"start": 0
}
},
"success": true
}And finally, we’re very keen on enabling security engineers to build their own integrations and scripts that talk with the HoneypotDB API. Our authentication API allows both user and account level API keys to be created with specific permissions, delivering programmatic machine-to-machine access to our product.
Search API
The backbone of our future intelligence and product capabilities is our Search API, a dynamic programmatic way to query the entire HoneypotDB dataset. We’ve built a custom query language that can be written in YAML or JSON that is powerful but easy to use to allow customers to build bespoke queries.
Example query using our query language:
---
name: An example query
query:
datetime:
gte: '2024-06-17T10:00:00.000Z'
lt: '2024-06-17T12:00:00.000Z'
filters:
- field: filebeat_agent.id
comparator: eq
value: 3b53c393-0fb0-4764-843d-06fff3652eb8
- or:
- field: hpdb.signal.auditd.type
comparator: eq
value: LOGIN
- field: hpdb.signal.auditd.type
comparator: eq
value: SYSCALL
We see customers using our Search API heavily to check the activity of an IOC (Indicator of Compromise), discover attack chains for attacks they’re related to and the trends of threats and CVEs.
We’re looking forward to expanding our Search capability with visualizations, dashboards and a powerful Python SDK,
Web App
We’re also excited to announce the first release of our web app – our powerful (soon) web console allowing customers to search our entire dataset and consume our intelligence, amongst other boring account admin things!
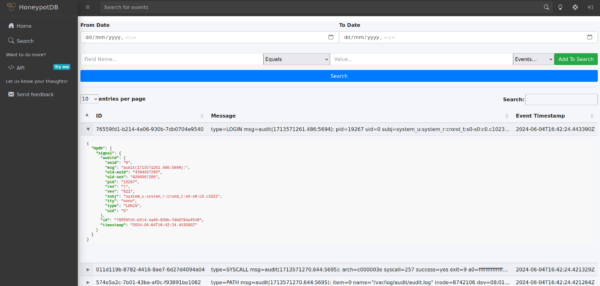
Our first release delivers a simple but easy to use web console that does just that, with the beginnings of our Search interface to query all our data with quick add filters and comparisons to pull back relevant results from our Search API, displayed pretty.
We have a vision for our web app to become a security team’s go-to tool to understand exactly how attacks are exploited, gather example logs to build detection rules and assess the real-world-risk for threats with our upcoming scoring capability.
Honeypot Deployment System
Sitting entirely behind the scenes, but still very exciting, is our completely automated honeypot deployment and management system. It enables us to rapidly deploy honeypots of any type at scale – a crucial capability to allow us to gather our data.
We’ve been testing and tweaking this system for a very long time, and it still has lots of advancements to come, but we’re excited to put it to a real-world test in this release.
Unfortunately, this isn’t something customers will get access to, but we do intend to surface an anonymized overview of our entire honeypot estate to showcase what CVE’s we’re capturing data for.
Low-Interaction Honeypots
Speaking of which, we’re kicking off our soon to be vast honeypot network with a collection of low-interaction honeypots for common protocols and applications. This will be a great test of numerous parts of our product, including:
- The honeypot deployment system’s ability to scale
- Our schema for defining a honeypot
- Accuracy of data ingest, normalization and indexing capabilities
- Capabilities of our Search API and Web app
We’ look forward to investigating the data we start to collect an our roadmap to deploying custom high-interaction honeypots for specific CVEs in the future.
Join the Beta to get access
We hope you’re as excited about the start of HoneypotDB as we are. Access to our current releases is exclusive for beta testers only.
If you want to join our mission to fix Threat Intelligence speak to us about becoming a HoneypotDB Beta Tester and signing up-to our Beta Program.
We’re building, a platform that captures real-world attacks for the latest CVEs to help analysts build detection rules and defenses.
We’re also planning to post regular updates on our development progress on this blog. So keep us bookmarked, or watch out for the post on socials.
Join The Beta
Get Early Access
Help make Threat Intelligence better!
Join our Beta Program for early access to our beta releases and influence the direction of our product.
Become a Beta TesterInfluence our roadmap
Have your say on the features, type of honeypots, integrations, and intelligence we build first.
Access Beta Releases
Get behind-the-scenes access to in-development releases of our product, provide feedback and bleeding-edge intelligence.
50% discount, forever
As a thank you, beta testers will receive a 50% discount on our future product’s pricing – lasting forever!
Disclaimers
The thumbnail photo of this post may have been generated using the Dall-E AI model.
The content of this post has been written by a human and may have been assisted by AI models for improvements in wording, structure and tone.


