Threat Intelligence
that’s actually useful
Clear and actionable threat intelligence based on the real-world
activity of cyber adversaries.
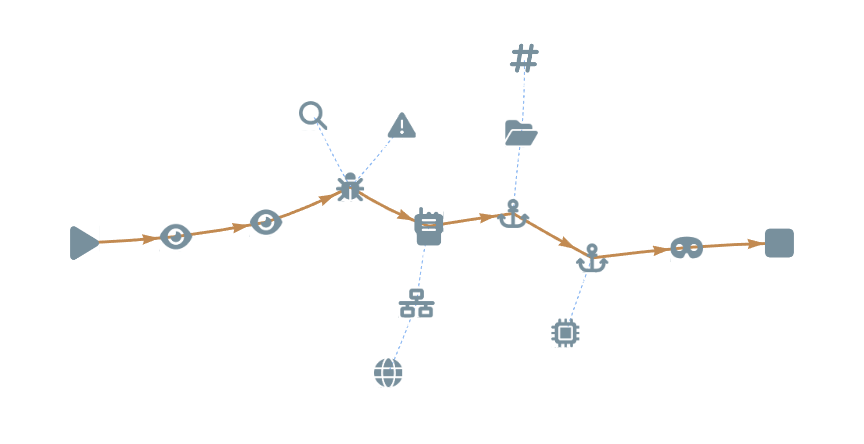
Clear attack visuals
Redefining Intelligence
We provide insight into the mechanics behind an attack, gaining a clear understanding of the threat, not just how to detect it.
Mapped to MITE ATT&CK and D3FEND
Clearly articulates the attack process
Contextulised with IOCs (Indicators of Compromise)
Real-World Attack Data
Backed by Data, not speculation
Tried and tested in the wild, all our intelligence is derived from real-world attack data, made open and accessible.
Complete access to all our data
Literally play SNAP, with our data and logs in your SIEM
Enriched with context, taxonomy and TTPs
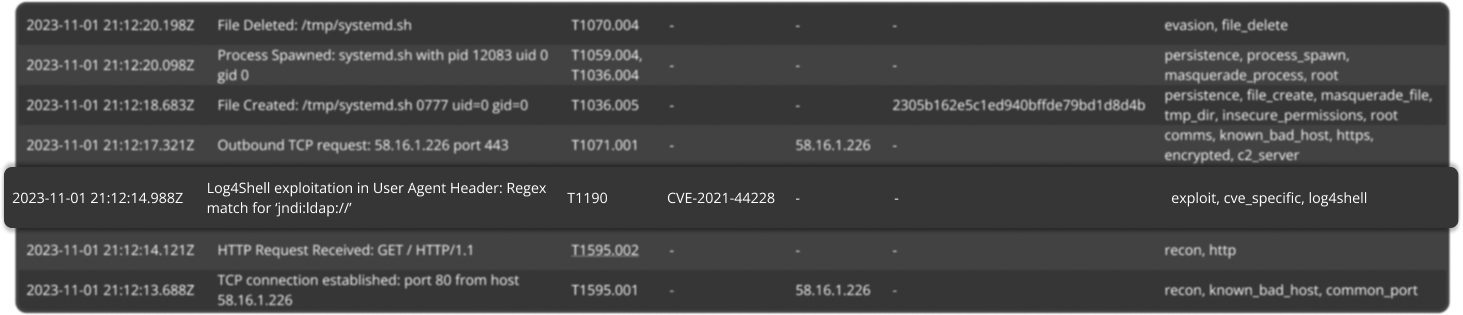
Data-driven Threat Intelligence
Backed by powerful capabilities
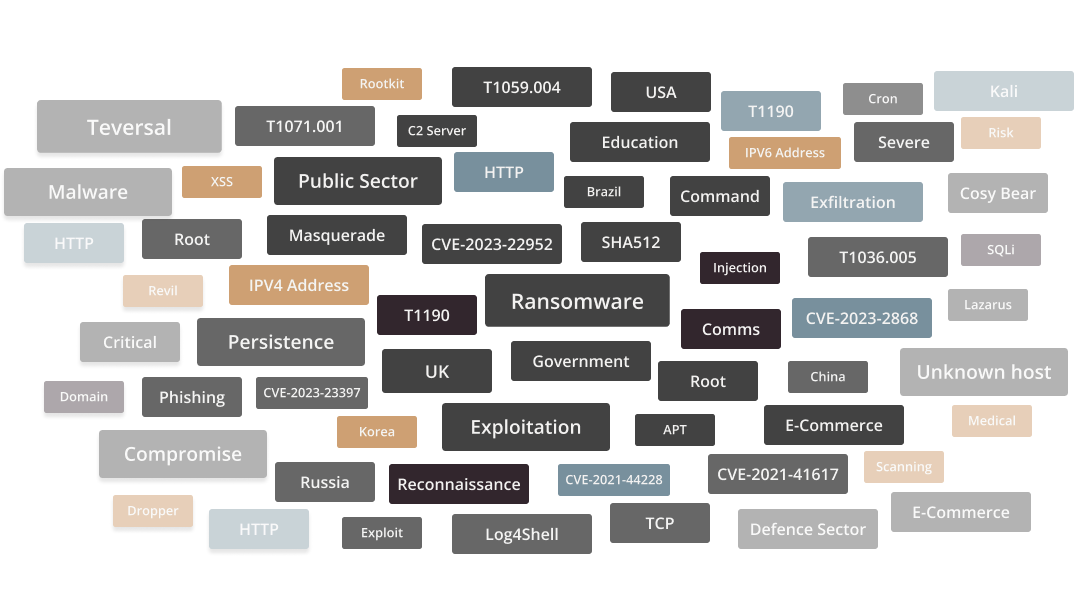
Focused on Context
Taxonomy that’s unrivaled
Enriching intelligence with metadata and tags to paint a clear picture of the surrounding attack landscape. Ingesting our intelligence is easy and genuinely adds value.
Filter by indicator type or attack
Highlight locations and threat actors
Understand attacks with TTPs and action tags
Understand the attack process
Transforming Junior Analysts into Senior Threat Hunters
Empower analysts with the skills to recognize and attack within a sea or raw logs and data.
Forget artificial intelligence, we’re creating Human Intelligence.
Real attack logs examples
Literally play SNAP, with our data and logs in your SIEM
Learn how to exploit a vulnerability to better defend it

Join The Beta
Get Early Access
Help make Threat Intelligence better!
Join our Beta Program for £1,000 granting early access to our beta releases and influence the direction of our product.
Become a Beta TesterInfluence our roadmap
Have your say on the features, type of honeypots, integrations, and intelligence we build first.
Access Beta Releases
Get behind-the-scenes access to in-development releases of our product, provide feedback and bleeding-edge intelligence.
50% discount, forever
As a thank you, beta testers will receive a 50% discount on our future product’s pricing – lasting forever!


