Building Threat Intelligence That’s Better
We’re not just another Threat Intelligence provider, we’re building a platform that focuses on the behaviors used during an attack, you know, the thing you need to build detection rules!
Tagged and Enriched
Obsessed with Context
Our IOCs and intelligence are heavily enriched and contextualized with behaviors, targeted technologies, trends, impact, and sophistication.
We make understanding the risk behind an IOC or vulnerability a lot easier.
Everything mapped to MITE ATT&CK and D3FEND
Linked to targeted technologies and industries
Highlights related attacks and likely compromises
Complete access to all our data
Access to real attack logs and examples
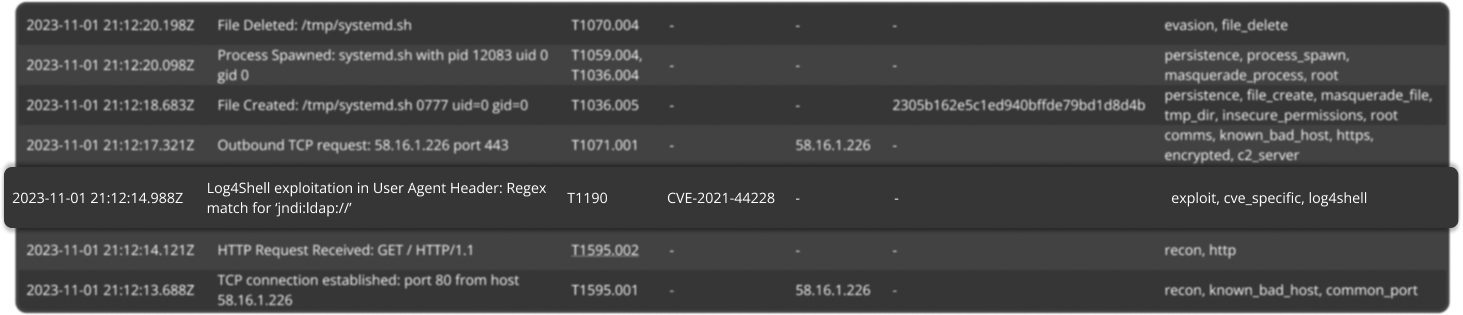
Captured attacks are logged and fully accessible in their raw form, building a repository of real attacks to build detection riles off.
Finally, data to create regex for your detection rules!
Access every process spawned, network event, command ran, and file accessed during an attack
Literally play SNAP, with our data and logs in your SIEM
Via our Search API or web console
Backed by real Data, not speculation
Captured from our network of Honeypots
Our data is captured from our global network of honeypots disguised as vulnerable technologies and industries, all owned and managed by us – we’re not installing anything into your network.
Backed by High Interaction Honeypots
Disguised as real technology stacks within a complete network
Nothing installed in your network means no risk
Data-driven Threat Intelligence
Backed by powerful capabilities

Query our data and discover attacks
Search
The backbone of our intelligence is our powerful Search API, allowing complete and unrivaled access to our repository of attack data.
Use our custom query language to discover all our data, from individual signals to fully categorized attack chains and events.

Actual samples used in the wild
Malware
All scripts executed, droppers used and malware detonated on our honeypots are captured and interrogated. They’re contextualized with IOCs, related attacks, and how they fit into observed attack chains.
They’re all available for download and offline analysis too.